Phishing campaigns that distribute commodity malware are common and ongoing problem for end users and corporations. In this article would like give you an illustration about one email that was part of a phishing campaign that distributes a very successful banking trojan malware known as Dyre or Dyreza. This trojan is quite sophisticated. Among other things is capable of stealing all kinds of credentials from the victim’s computer. It can also redirect victim’s traffic to sites controlled by the threat actors using man-in-the-browser functionality. This allows interception and manipulation of traffic that is supposed to be delivered to legitimate sites. Dyre has remote access functionality that allows the threat actor to connect to websites trough the victim computer.
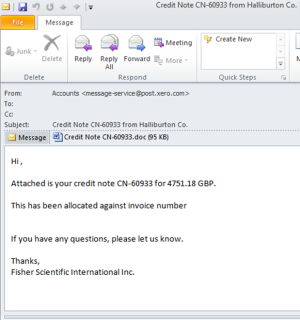
The distribution methods observed is the past are mainly done using phishing emails that include a malicious Microsoft Office document attached. It normally includes a Microsoft Word or Excel document with macros. The image below illustrates one of these samples where the sender falsely mimics a legitimate business transaction. This well-crafted email attempts to lure the recipient into opening the malicious attachment.
Noteworthy is that the threat actors behind the malware distribution operations go to great lengths ensuring the files are not detected as malicious by the different security mechanism such as Anti-Spam, Anti-Virus and Sandboxes. Is quite normal when submitting this malicious Office documents to Virus Total to have less than 10% detection rate and being rated benign by Sandboxes.In this example as seen in the picture below, the user when opening the email attachment is presented with the information that the document is encrypted with RSA algorithm and the user needs to enable macros in order to see its content.
The document is of course not encrypted and this is a social engineering technique to trick the users to run the malicious macro. Allowing macros to run causes the malware to be extracted and executed in the victim system.
So what makes this document different than the others recently seen? The difference is in the weaponization mechanism that was used. Traditionally, these malicious Office documents have encoded and obfuscated macros. These macros when executed will connect to a site and download the malicious executable. However, in this case the document contains an obfuscated macro but the executable is embedded within the document. This reduces the steps needed for infection and might increase the infection rate.
What tools and techniques one could use to unravel what is inside the document?
For malicious document analysis, REMnux and the cheat sheet created by Lenny Zeltser are a fantastic companion. On REMnux v6 one of the new tools pre-installed is the python-oletools toolkit. This toolkit was created by Philippe Lagadec based on the work created by John William Davison on officeparser. The tool among other things can parse and extract VBA Macros from Microsoft Office documents. It supports a variety of Microsoft Office documents and it can be very handy for this type of malicious documents. We start with the usage of olemeta.py to view the document metadata. In this case we could see codepage 1252 which might indicate where the document was fabricated. Then we run oleid.py which gives us a very good overview about the capabilities inside the document. In this case we could observe that the document contain VBA macros and OLE embeded objects. These indicators definitely need a deeper look.
We start by looking at the VBA macro. The following picture illustrates the output given by olevba.py after analyzing the malicious Office document. It shows the actual macro and one could see that is obfuscated. In addition the tool gives its interpretation of the different functions used in the macro. Many of the functions used are considered suspicious.
Based on this information we can see that the document contains a obfuscated VBA macro that presumably creates RTF files (300.rtf and 301.rtf) and extracts an executable called n1.exe.
To further dig into these artifacts we will use another great tool. Oledump created by Didier Stevens. This tool allows you to analyze OLE files. As stated in the manual page: “Many file formats are in fact OLE files, like Microsoft Office files, MSI files. Even the new Microsoft Office Open XML format uses OLE files for VBA macros”. Another powerful tool created by Didier that even supports decoders and plugins such as Yara rules. One of the Yara rules is based on the work made on OfficeMalscanner by Frank Boldewin that can find shelcode, PE-files and other embedded streams inside Office documents.
To verify our suspicious we use oledump.py with a yara rule that detects the presence of PE files inside documents. The output confirms that an executable was found inside the document.
We can now extract the executable. The stream that triggered the Yara rule is the stream 11. Once again using oledump.py we can extract the binary and redirected to a file for further analysis.
With the executable extracted we can now start using static and dynamic analysis techniques to determine the malware capabilities and extract IOCs that can be used to across our logs and network to find infected systems. This will be left for another blog post.
E-mail continues to be the weapon of choice for mass delivering malware. The tools and techniques used by attackers continue to evolve and bypass all the security controls in place. From a defense perspective, the US-CERT put together excellent tips for detecting and preventing this type of malware and to avoid scams and phishing attempts applicable to home users and corporations.
MD5 of the files used in this exercise:
Evil.doc : dd3cd493aa68f55d1df442873ad2b2e8
Evil.bin : 27079661fb498dcf18194f45a4171492






Can you send me this document? Thank you in advance.
LikeLike
Sure, have fun!
LikeLike
Hi Luis, this is a great post. Can you please send me the document as well? I would like to analyze the doc’s payload. Thanks in Advance.
LikeLike
Sure, sent to your mailbox.
LikeLike
Is there a way to make this real-time? Do we have to manually run these tests every time?
LikeLike
Hi, In this case the tools and techniques used were manual because it allows me to practice, learn and is also useful in case the malware sample has sandbox evasion techniques. For automated analysis, you could try Cuckoo Sandbox which is opensource and a fantastic tool.
LikeLiked by 1 person