E-mail continues to be the weapon of choice for mass delivering malware. The tools and techniques used by attackers continue to evolve and bypass all the security controls in place. These security controls could be a simple home based UTM device or a big corporation security infrastructure with all kinds of technology. Social engineering methods, combined with latest encoding and obfuscation techniques allow e-mails to be delivered straight to the end user mailbox. These phishing e-mails attempt to steal confidential data such as credentials using all kinds of deception techniques to lure users to click on links or open documents or give their information. In the last days I came across some of these documents. The below steps describe the mechanism behind one of these documents (MD5: 4a132e0c7a110968d3aeac60c744b05a) that when opened on Microsoft Office lure the victim to enable macros to view its content. Even with macros disable many users allow the macro to execute. What happens next?
- The malicious document contains a VBA macro.
- The macro is password protected. The protection can be bypassed using a hex editor and replacing the password hash with a known password hash to see its contents.
- When executed the VBA macro writes 3 files on disk. A batch file”ntusersss.bat”, a VBS script “ntuserskk.vbs” and a powershell script “ntusersc.ps1”.
- It invokes cmd shell and executes the batch file which calls the VBS script
- Microsoft Script Host (cscript.exe) is invoked and the VBS script is executed which calls the powershell script
- Power shell script is executed and it downloads the malicious EXE
- The malicious file is stored on disk and renamed to crsss2.exe
- The trojan is executed and the machine is infected.
The following picture illustrates the previous steps.
The downloaded malware is very sophisticated and is known to be a variant of the Feodo ebanking trojan (aka Cridex or Bugat). This trojan contains advanced capabilities but the main feature is to steal credentials by performing men in the browser attacks. These credentials are then used to commit ebanking fraud . After execution, the malware contacts the Command and Control server and the machine becomes part of a botnet and starts capturing and stealing confidential data.
Another new document used recently in several phishing campaigns it also uses a VBA macro inside the word document (MD5: f0626f276e0da283a15f414eea413fee). But this time the VBA code is obfuscated. Using the Microsoft macro debugger its possible to execute in a step-by-step fashion and determine what it does. Essentially it downloads a malicious executable file from a compromised website and then it executes it.
Again, after execution it contacts its Command and Control via HTTP. The computer will be part of a Botnet and it will start to steal credentials and other confidential data.
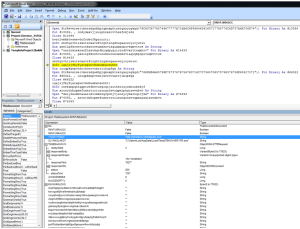
Below a visual analysis of the malware behavior starting with the Winword execution. This graph was made using ProcDOT which correlates Sysinternals Procmon logfiles with packet captures to create an interactively graph. A great tool created by Christian Wojne from the Austrian CERT. This can be of great help for a faster malware behavior analysis. It is also unbelievable to visualize how complex is malware these days. I will leave a how-to on how to produce these graphs for other blog post.

From a defense perspective, the US-CERT put together excellent tips for detecting and preventing this type of malware and to avoid scams and phishing attempts applicable to home users and corporations. Note that these documents were not detected by the AV engines at the time the phishing campaign was seen. Virustotal was reporting less than 5% detection rate. Even running on a limited privileges user account the attack would still be successful. A key recommendation is to use Enhanced Mitigation Experience Toolkit 5.0 from Microsoft as part of your layered defense.
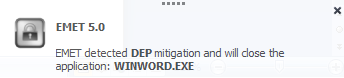 This is a free product from Microsoft for the endpoint and will prevent the execution of the attacks described previously and many others. Exploit mitigation technologies do not guarantee that vulnerabilities cannot be exploited. However, they raise the bar and increase the costs for the attacker to make exploitation successful by making it harder to be executed. On a windows 7 SP1 with EMET 5, when opening the documents and running the malicious VBA macros, EMET would prevent its execution.
This is a free product from Microsoft for the endpoint and will prevent the execution of the attacks described previously and many others. Exploit mitigation technologies do not guarantee that vulnerabilities cannot be exploited. However, they raise the bar and increase the costs for the attacker to make exploitation successful by making it harder to be executed. On a windows 7 SP1 with EMET 5, when opening the documents and running the malicious VBA macros, EMET would prevent its execution.
Email attachments can be dangerous. Use caution with Email attachments!


I just received a spam Doc file which I am sure is malware. But I cannot for the life of bypass the Macro Passwords to view them. I loaded them in the hex viewer but have no luck finding value. Could I send this to you to see how to decode this file? Thanks
LikeLike
Have you tried Oledump from Dider Stevens? or OfficeMalscaner from Frank Boldewin? You can also try to upload the sample to a sandbox like Malwr.com …
What is the md5 of the file?
LikeLike
I have downloaded EMET 5.2 and installed it in a VM to test to see if it will prevent the execution of the latest Word doc macro malware. I have enabled the highest security settings and added these “modules”, flash*.ocx; jscript*.dll;vbscript.dll; to both EAF+ and ASR and have not been able to prevent the macros from creating and executing the .bat, .vbs, and .ps1 files that are then executed (added those modules as per this page – http://www.wilderssecurity.com/threads/emet-enhanced-mitigation-experience-toolkit.344631/page-24). I had high hopes that EMET might be able to prevent this but it does not seem to. Any thoughts or advice?
LikeLike
Hello Robert, that is interesting … I just started my VM running:
Microsoft Windows Enterprise 7 version 6.1.7600
Microsoft Office 2007 12.0.4518
EMET 5.0.5324
And EMET was able to detect/mitigate the macro to run successfully on the following malicious documents (Word and Excel):
MD5: E4A6063140A90F2008C4ABA4C1DFFCDE
MD5: 4A132E0C7A110968D3AEAC60C744B05A
MD5: AC2BE7A5276E3EC0EFACB1B88375F238
MD5: 242F0E867012C266879215559E8742DF
On EMET I had the default mitigation options where all Office executables are considered. In this case the protection that triggers is the DEP one. In your settings are the office executable being protected by mitigation options on EMET?
LikeLike
Luis,
My VM is running WIndows 7 Professional 6.1.7601
Microsoft Office 2007 12.0.6718.5000
EMET 5.2.5546.19547
Yes, the Office applications are protected by EMET (green check mark next to WINWORD.EXE when it is launched). I have tried the “recommended settings” and the “maximum security” settings. For WINWORD.EXE everything but EAF+ is checked and I even tried checking that.
The file that I have been using is
MD5: D600952252D62D1B909356CF49A3BE50
A Word doc received last Wednesday, 3/18/2015
I just tried it again and there is no attempt to stop anything that the malware does.
Command shell
PING
Creation and execution of BAT file, VBS file, PS1 file, etc.
Now … after letting it sit for a bit WORD has crashed and there is an EMET message but this is a minute or more after the malware has launched, executed and downloaded everything. Not much help to kill WORD after all the damage is done.
Your thoughts?
Thanks!
LikeLike