The concept behind physical attacks – a.k.a. Evil Maid – are not new or sophisticated. However is important to raise awareness about how someone with motive, opportunity and means could easily pull off an attack against a system in which there is physical access. Such attack can, for example, be used to steal the users password file from the operating system. These file contains the users passwords representations using a one way hashing function. Usually the operating systems password file is well protected and difficult to steal but someone with physical access could easily get to it.
On a typical Windows machine the hashed password file is stored locally in the security account manager (SAM) database located in the windows/system32/config/ folder or remotely in Active Directory servers. Furthermore, the local SAM database could be encrypted with a additional 128 bit encryption using SYSKEY method. On a typical Linux machine the hashed passwords are stored in the shadow file located in /etc/. In addition, there is the passwd file which contains the account information. Besides that, Windows hashes are not salted. Unix hashes are. Without salt, users with the same password will have the same hash representation and it will increase the likelihood for someone to obtain the password and/or cracking it using rainbow tables.
After obtaining the password file with the passwords representations in form of hashes, someone could use different methods to crack the passwords. For example, one could use a dictionary, brute force or hybrid attack techniques among others.
The below scenario illustrates a step-by-step physical attack against a Windows system that contains un-encrypted hard drives. This system uses the NT hashing function in conjunction with SYSKEY encryption to store the password representation. To give some more background, on Windows passwords the Windows NT operating systems up to and including Windows Server 2003 store two password hashes, the LAN Manager (LM) hash and the Windows NT hash. Starting in Windows Vista, the capability to store both is there but disabled by default. The NT hash is a MD4 hash of the plaintext password. It supports all Unicode characters and passwords up to 256 characters long.
Scenario: Justin Case, a high-priced lawyer and an operative for V.I.L.E. found that ACME is working on a new high-profile deal. Justin Case wants to get the hands on that information to sell it to the competitors. He knows that Ivan Idea is going to fly to Paris to have an important meeting at known hotel in city center. Ivan Idea will be taking ACME laptop with him. Justin Case mission is to sneak into the hotel room of Ivan Idea and get his ACME laptop passwords.
How can Justin Case accomplish this?
- Justin Case prepares a bootable USB stick or CD.
- Justin Case sneaks into Ivan Idea room and boot the laptop with the bootable USB stick.
- After 1 or 2 minutes the laptop is running a shell with full access to hard drives (NTFS volumes).
- Using the command prompt Justin Case steals the SAM database and the SYSTEM registry file.
- Justin Case goes back into his office and loads the SAM database and the SYSKEY into CAIN and export the NT hashes into a file.
- Justin Case launches a dictionary attack and brute force attack against the NT hashes using Hashcat taking advantage of powerful GPUs (HD Radeon Dual 7990).
Let’s look into each one of these steps in detail:
First, to create a bootable USB/CD there are a variety of methods and tools. In this case he will use the Offline NT Password & Registry Editor tool created by Petter N Hagen. Noteworthy, that any Linux live CD distro will do the job such as Ophrack or BackTrack. The files needed to create a bootable USB stick are available here and the steps need are well documented.
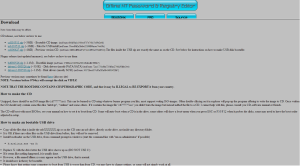
Second, Justin Case sneaks into Ivan Idea room and boot’s the laptop with a USB stick containing the Offline NT Password & Registry tool. He could typically just press the boot order key during P.O.S.T. and choose to boot from USB. The following image is the tool first screen to choose the boot options.

After boot, the tool automatically detects the hard drives and asks to choose which hard drive you want to mount.

Then he selects which path to search for the SAM database and the SYSTEM registry file. The default option will work on typical Windows installations.

Then, the selected hard drive is mounted and he needs to choose what is the path for the SAM and registry files.

Forth step consists of running a command prompts and copying the SAM Database and the SYSTEM registry file into the USB stick. Both files need to be copied, as the SYSTEM file contains the SYSKEY with which to decrypt the hashes from the SAM database. Eventually, with this tool, he could do a password reset and change the password for the admin user. However in this case Justin Case wants to be stealth as possible without leaving trace that he got access to the system. As any other Linux system he opens another terminal window with CTRL+F2. Then he can mount the USB drive into /mnt folder and copy the SAM database and SYSTEM registry system file.
#mount /dev/sdb1 /mnt
#cp /disk/WINDOWS/system32/config/SAM /mnt
#cp /disk/WINDOWS/system32/config/SYSTEM /mnt
#umount /mnt
He turns off the laptop and leaves.
Fifth step, Justin Case goes back into his office and loads the SAM database and the SYSKEY into CAIN – extremely rich tool made by Massimiliano Montoro – and export the NT hashes into a file.
To do this, in CAIN he goes into the Cracker tab in. Then on the left he selects the NTLM Hashes and then on the right, right click and select Add to List. Here choose to Import Hashes from SAM database and choose the SAM file. Then in the Boot Key field select open the SYSTEM Registry file and insert the value.

After clicking next, the accounts and respective password representations will show.

Right click – Export. This will save the hashes in L0pthCrack format. The file contents will be like the following:
Administrator:"":"":AAD3B435B51404EEAAD3B435B51404EE:DD21163C6AB4DFF1517F0BA7464A511D
Guest:"":""::
Ivan.Idea:"":"":AAD3B435B51404EEAAD3B435B51404EE:C0D303C74587269C9557C706365BA8F0
Dee.Plomassy:"":"":AAD3B435B51404EEAAD3B435B51404EE:250CFEAA42D97F8EA0D30400E8016D29
Herman.Nootix:"":"":AAD3B435B51404EEAAD3B435B51404EE:09238831B1AF5EDAB93C773F56409D96
Polly.Tix:"":"":AAD3B435B51404EEAAD3B435B51404EE:1F255EA9557F52407F4290C904447F1A
The sixth step consists of using two techniques for cracking the passwords. The first technique, dictionary based, is the fastest. It consists in testing all the words in a dictionary file against the hashes. Basically every word in the dictionary is hashed and then compared with the hashes from the password file. If this matches then he has found the password. Other technique is the brute force attack which is the most powerful but the slowest. It consists in testing all the possible combinations until it cracks it. To execute this methods there are several tools available such as CAIN or John the Ripper. In this case we want to take advantage of graphic cards (GPU) computing power versus using CPU to compute and crack the hashes.
To accomplish this, Justin Case launches a dictionary attack and then a brute force attack against the NT hashes using Hashcat – An extremely fast and powerful password cracking tool made by Atom – using strong GPUs.
The first command will be executed to run a dictionary attack (-a 0) with the hashing algorithm type NTLM (-m 1000) using the well known rockyou wordlist containing over 14 million passwords. This attack will run for an incredible velocity of 32K hashes per second. It took 5 seconds with a HD Radeon Dual 7990 to go over all the words in the dictionary file, hash them and comparing the hash with the password file. In this case 2 passwords were found.
C:\Users\Justin.Case> oclHashcat-plus64.exe -a 0 -m 1000 ACME-NT-Hashes.txt rockyou.txt
oclHashcat-plus v0.15 by atom starting...
Hashes: 5 total, 1 unique salts, 5 unique digests
Bitmaps: 8 bits, 256 entries, 0x000000ff mask, 1024 bytes
Rules: 1
Workload: 256 loops, 80 accel
Watchdog: Temperature abort trigger set to 90c
Watchdog: Temperature retain trigger set to 80c
Device #1: Tahiti, 2048MB, 900Mhz, 32MCU
Device #2: Tahiti, 2048MB, 900Mhz, 32MCU
Device #1: Kernel ./kernels/4098/m1000_a0.Tahiti_1268.1_1268.1 (VM).kernel (477800 bytes)
Device #1: Kernel ./kernels/4098/bzero.Tahiti_1268.1_1268.1 (VM).kernel (30444 bytes)
Device #2: Kernel ./kernels/4098/m1000_a0.Tahiti_1268.1_1268.1 (VM).kernel (477800 bytes)
Device #2: Kernel ./kernels/4098/bzero.Tahiti_1268.1_1268.1 (VM).kernel (30444 bytes)
Cache-hit dictionary stats rockyou.txt: 139921519 bytes, 14343298 words, 14343298 keyspace
250cfeaa42d97f8ea0d30400e8016d29:StR0ngP4ss
09238831b1af5edab93c773f56409d96:P4$$w0rd
Session.Name...: oclHashcat-plus
Status.........: Exhausted
Input.Mode.....: File (rockyou.txt)
Hash.Target....: File (ACME-NT-Hashes.txt)
Hash.Type......: NTLM
Time.Started...: Mon Oct 14 20:48:39 2013 (4 secs)
Time.Estimated.: 0 secs
Speed.GPU.#1...: 17232.7 kH/s
Speed.GPU.#2...: 15074.3 kH/s
Speed.GPU.#*...: 32307.0 kH/s
Recovered......: 2/5 (40.00%) Digests, 0/1 (0.00%) Salts
Progress.......: 14343298/14343298 (100.00%)
Rejected.......: 1599/14343298 (0.01%)
HWMon.GPU.#1...: 36% Util, 48c Temp, 46% Fan
HWMon.GPU.#2...: 64% Util, 66c Temp, N/A Fan
Started: Mon Oct 14 20:48:39 2013
Stopped: Mon Oct 14 20:48:44 2013
This attack is very effective and fast. But, not all passwords are on the dictionary file. As result Justin Case uses a brute force technique to pursue his goal. The second command will be executed to run a brute force attack (-a 3) with the hashing algorithm type NTLM (-m 1000). This attack will run for an incredible velocity of 12652M hashes comparison per second.
C:\Users\JustinCase>oclHashcat-plus64.exe -a 3 -m 1000 ACME-NT-Hashes.txt
oclHashcat-plus v0.15 by atom starting...
Hashes: 5 total, 1 unique salts, 5 unique digests
Bitmaps: 8 bits, 256 entries, 0x000000ff mask, 1024 bytes
Workload: 256 loops, 80 accel
Watchdog: Temperature abort trigger set to 90c
Watchdog: Temperature retain trigger set to 80c
Device #1: Tahiti, 2048MB, 900Mhz, 32MCU
Device #2: Tahiti, 2048MB, 900Mhz, 32MCU
Device #1: Kernel ./kernels/4098/m1000_a3.Tahiti_1268.1_1268.1 (VM).kernel (135208 bytes)
Device #1: Kernel ./kernels/4098/markov_le_plus_v2.Tahiti_1268.1_1268.1 (VM).kernel (134476 bytes)
Device #1: Kernel ./kernels/4098/bzero.Tahiti_1268.1_1268.1 (VM).kernel (30444 bytes)
Device #2: Kernel ./kernels/4098/m1000_a3.Tahiti_1268.1_1268.1 (VM).kernel (135208 bytes)
Device #2: Kernel ./kernels/4098/markov_le_plus_v2.Tahiti_1268.1_1268.1 (VM).kernel (134476 bytes)
Device #2: Kernel ./kernels/4098/bzero.Tahiti_1268.1_1268.1 (VM).kernel (30444 bytes)
[s]tatus [p]ause [r]esume [b]ypass [q]uit =>
c0d303c74587269c9557c706365ba8f0:bigideas
Session.Name...: oclHashcat-plus
Status.........: Running
Input.Mode.....: Mask (?1?1?1?1?1?1?1?1) [8]
Hash.Target....: File (ACME-NT-Hashes.txt)
Hash.Type......: NTLM
Time.Started...: Fri Oct 18 20:57:15 2013 (5 secs)
Time.Estimated.: Sat Oct 19 01:50:21 2013 (4 hours, 53 mins)
Speed.GPU.#1...: 6378.8 MH/s
Speed.GPU.#2...: 6378.9 MH/s
Speed.GPU.#*...: 12757.7 MH/s
Recovered......: 0/5 (0.00%) Digests, 0/1 (0.00%) Salts
Progress.......: 69457674240/218340105584896 (0.03%)
Rejected.......: 0/69457674240 (0.00%)
HWMon.GPU.#1...: 86% Util, 50c Temp, 47% Fan
HWMon.GPU.#2...: 97% Util, 70c Temp, N/A Fan
[s]tatus [p]ause [r]esume [b]ypass [q]uit =>
In this case another password has been revealed. In a brute force attack using a charset that contains all upper-case letters, all lower-case letters and all digits for a password length of 8 we have to iterate trough 62^8 combinations – 26 upper-case + 26 lower-case + 10 digits = 62 ^ the number of characters – . This is a huge number but with GPUs this attack can be feasible in a matter of hours. However, when you increase the length to 12 characters it could take years to crack using brute force techniques.
As you can see, it is only a matter of time before all possible characters combinations are tested and the password is exposed. Of course, depending on the length and complexity of the password and the hashing algorithm used the cracking could take minutes, years or decades. One of the countermeasures against this type of attacks is a strong password policy. The policy should dictate that a password must be at least eight characters, with upper and lowercase letters and two special characters (*#$@). It should also have an expiration date and reuse policy. Long passwords which contain special characters are hard to crack and increases the likelihood of the attacker moving on to a easier victim.
Other countermeasures that reduce the exposure to this attack is using a combination of other authentication techniques also known as multi-factor authentication. The password authentication mechanism is based on something that a user normally knows, this is a single factor authentication. Other techniques are based on something the user is – biometric – or something the user has – an access token -. Combining multiple factors of authentication, one could build a strong authentication scheme very costly to break. Plus, you could protect your BIOS with a password and prevent the computer to boot from USB/CD increasing the difficulty of this attack.
In part II of this article I aim to write about how can Justin Case launch a similar attack but against a system with the hard drive encrypted with Truecrypt using technique described by Joanna Rutkowska.
Other References:
http://www.irongeek.com/i.php?page=videos/password-exploitation-class