[Part 1 illustrates a series of very useful tools and techniques used for dynamic analysis. Security incident handlers and malware analysts can apply this knowledge to analyze a malware sample in a quick fashion using the multi-purpose REMnux v5. This way you can extract IOCs that might be used to identify the malware across your defense systems and aid your incident response actions. ~Luis]
[Part 1 illustrates a series of very useful tools and techniques used for dynamic analysis. Security incident handlers and malware analysts can apply this knowledge to analyze a malware sample in a quick fashion using the multi-purpose REMnux v5. This way you can extract IOCs that might be used to identify the malware across your defense systems and aid your incident response actions. ~Luis]
Malware analysis is a interesting topic nowadays. It requires a fairly broad of knowledge and practical experience across different subjects. My background is in systems and infrastructure which means I am more confident with the dynamic analysis methodology than the static analysis one. Some of the readers have similar background. However, if you are willing to roll your sleeves and spend time in order to learn and be proficient with the different tools and techniques static analysis can done – hopefully will write about basic static analysis in a near future. Additionally is intellectually challenging.
One of the goals of performing malware analysis is to determine the malware actions and get insight into its behavior and inner workings by analyzing its code. By doing this we can find answers to pertinent questions such as:
- What are the malware capabilities?
- What is the worst it can do?
- Which indicators of compromise (IOC) could be used identify this malware in motion (network), at rest (file system) or in use (memory)? – These IOCs can then be used across our defense systems and in our incident response actions.
The process consists of executing the malware specimen in a safe, secure, isolated and controlled environment.The dynamic analysis methodology allows you to determine the malware behavior and how it interacts with the network, file system, registry and others. In this post I go trough a technique to determine its behaviour at the network level. In this way we can start answering the previous questions.
How?
A simple and effective manner to execute malware analysis in an safe, isolated and controlled fashion would be to use a second hand laptop with enough RAM and fast I/O like a SSD drive. Then on top of it a virtualization software. My personal preferences goes VMware Workstation due to the wide range of operating systems supported, and affordable price. Essentially two virtual machines. One machine running the resourceful and multi-purpose REMnux v5.
For those who don’t know, REMnux is a fantastic toolkit based on Ubuntu created by Lenny Zeltser that provides an enormous amount of tools preinstalled to perform static and dynamic malware analysis. The tools installed have the ability to analyze Windows and Linux malware variants. You can download it from either as a Live CD or a preconfigured virtual appliance for Vmware or VirtualBox from here.
The second machine will be running Windows XP or 7 32 Bits. That will get you started. Then configure the environment and install the required tools on the disposable – relying heavily on VMware snapshots – Windows machine.
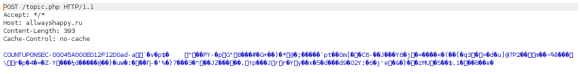
In the first technique, I want REMnux to act as gateway, dns server and proxy – including SSL – . This will allow us to intercept all network communications originating from the infected machine. The following picture illustrates the methodology for dynamic analysis.
The illustration should be self-explanatory. In this manner, any DNS request made by the infected machine will be redirected to the REMnux. If the malware is not using DNS but using hardcoded IP addresses, the requests will go through the default gateway which is pointing to the REMnux. The REMnux by its turn will have iptables configured to redirect all received traffic either on port TCP 80 or 443 to TCP port 8080. On this port – TCP 8080 – Burp Suite is listening as a transparent Proxy. In this way you will have visibility and control into all network communications initiated by the infected machine.
On REMnux the steps to perform this configuration are:
- Define the Network adapter settings on VMware Workstation to be in a custom virtual networkg., VMnet5.
- Define a static IP
- Start FakeDNS to answer any DNS requests.
- Start HTTP daemon to answer HTTP requests.
- Redirect HTTP and HTTPS traffic to port TCP 8080 by configuring redirect rules via iptables.
- Intercept HTTP requests using BURP Suite in Invisible mode on port 8080
- Optionally you run tcpdump to capture all the networking traffic (allows you to create IDS signatures).
Te necessary commands to perform steps 3 to 6 are:
remnux@remnux:~$ sudo fakedns 192.168.1.23 dom.query. 60 IN A 192.168.1.23
Open another shell:
remnux@remnux:~$ httpd start Starting web server: thttpd.
remnux@remnux:~$ sudo sysctl -w net.ipv4.ip_forward=1 net.ipv4.ip_forward = 1
remnux@remnux:~$ sudo iptables -t nat -A PREROUTING -i eth0 -p tcp --dport 80 -j REDIRECT --to-port 8080 remnux@remnux:~$ sudo iptables -t nat -A PREROUTING -i eth0 -p tcp --dport 443 -j REDIRECT --to-port 8080
remnux@remnux:~$ sudo iptables -t nat -L
Chain PREROUTING (policy ACCEPT) target prot opt source destination REDIRECT tcp -- anywhere anywhere tcp dpt:https redir ports REDIRECT tcp -- anywhere anywhere tcp dpt:www redir ports REDIRECT tcp -- anywhere anywhere tcp dpt:www redir ports REDIRECT tcp -- anywhere anywhere tcp dpt:https redir ports remnux@remnux:~$ burpsuite [1] 8912
Then, on Windows the initial steps are:
- Define the Network adapter settings in the VMware to be in the same custom virtual network as the REMnux.
- Configure IP address in the same range as the REMnux
- Configure the DNS server to point to the REMnux
- Define the default GW as being the REMnux
- Test the network settings
- Create a VMware snapshot
- Move the malware sample to the machine
- Start necessary tools (if needed)
- Execute the malware sample
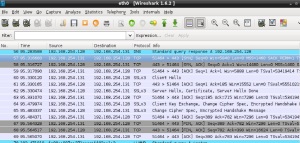
After having the machines ready you can move your malware sample to the disposable Windows machine and execute it. In this case I executed a malware variant of Torrentlocker. The result is shown in the following picture:
- There is a query from the Windows machine to the DNS server asking the A record of the address allwayshappy.ru
- FakeDNS answers back with the IP of the REMnux
- Windows machines establishes a SSL connection to the IP REMnux on port 443 which is redirected trough iptables to port 8080
- The traffic is Intercept by Burp Suite and can be seen and manipulated in clear.
- The request can be forwarded to localhost on port 80 to fake an answer.
Following the first request, this malware performs a second request, potentially sending some more data. Unfortunately the request is encrypted – that would be a good challenge for static analysis!
As you could see in a quick manner you could determine that the malware tries to reach out to a C&C. This type of knowledge can then be used to find other compromised systems and start your incident response actions.
You might see this as a time-intensive process that does not scale – think a company that needs to analyse hundreds of samples per month, week or per day – solution is automation. Several automated malware analysis system have appeared over the last years such as CWSandbox, Norman Sandbox, Anubis, Cuckoo and others. Essentially these systems load the malicious binary into a virtual machine and execute it. During execution all the interactions with I/O, memory, registry and network are tracked and then a report is produced. This greatly reduces the costs of malware analysis. However, is good to understand how to do manual analysis because many times the malware samples only trigger on specific conditions or bypasses the sandboxes. In addition you start to be proficient on different tools and techniques!
References:
SANS FOR610: Reverse-Engineering Malware: Malware Analysis Tools and Techniques