[Editor’s Note: In the article below, Angel Alonso-Parrizas who is a SANS GSE certified, illustrates a series of very useful tools and techniques that security and malware analysts can apply to analyze mobile code malware. This way you can get familiar with malware specimens and analyze it on your own. Using free tools suite like Remnux or Mobisec you can put malware under a controlled environment and determine its purpose and functions. ~Luis]
Last week
Lenny Zelster released version 4 of
REMnux, a Linux distribution thought to perform malware analysis.
REMnux includes a
set of tools to facilitate and speed up the analysis and although REMnux is not designed to perform Android malware analysis, it is possible to use some of the tools for this purpose.
On the other hand the guys from
Secure Ideas have deployed a Linux distribution named
MobiSec which is designed to evaluate and analyze the security of mobile devices and the applications running on them. Also, it has many tools, emulators, etc.
The idea of this post it to show both distributions and combine the functionalities of them with a simple example for Android. The purpose isn’t to do an exhaustive malware analysis, but explain how these distributions can be used to perform part of the behavior analysis.
It is possible to download REMnux in OVF/OVA which can be imported in VMWare or VirtualBox. On the other hand MobiSec requires to download the ISO and to install it manually . Once both OS have been installed, and on account that we are dealing with malware, it is key to setup the network isolated, without internet access, hence in ‘Host only’ mode. In order to facilitate the analysis, we have to setup the DNS and Gateway of MobiSec to REMnux’s IP.
Mobisec, beside other tools, it includes several version of Android emulator which facilitates a lot the work when you need to test something in Android in a quick way, because there is not need to setup anything. For this example we will use version 4.0.3
Next step is to push the malware into the emulator which is running in MobiSec. In this example we will download the sample from http://contagiominidump.blogspot.com.es to the phisicall machine and afterwars it will be copied to MobiSec through SCP. The malware chosen is l
Android.Exprespam. The last step is to install the file through the ‘adb’ commands (adb install).

In the meantime, and before execute the malware in the emulator, let’s prepare REMnux. REMnux allows to run services (like a honeypot) to interact with the malware. For example, we can run a DNS server to resolve domain, IRC server, a SMTP server or a HTTP server
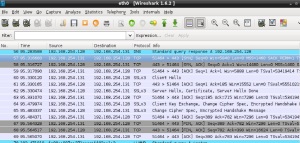
First step is to run ‘fakedns’ which will resolve any domain to REMnux IP and at the same time launch Wireshark to have visibility on what’s going on
In this case we can see that the malware is asking for the domain ftukguhilcom.globat.com and REMnux is replying with the IP of itself.
We can observe in Wireshark that the malware is trying to make a HTTPS
connection, which is RST by REMnux as there is no service running on that port.
Next step is to emulate the HTTPS server in order to see the traffic. REMnux includes an HTTP server and stunnel, which permits to combine both tools to provide an HTTPs server. To do that it is necessary to launch the server with ‘httpd start’ and setup stunnel with an autosigned certificated.
If we look to the HTTP logs we can see there is not any HTTP request. This is because it is necessary to accept the autosigned certificate when accessing through HTTPs. This might be because the malware checks the certificate, as an additional control, or the malware is using Android web browse which is not imported in the repository.
If it were the second case, it would be possible to import the certificate in Android’s repository and avoid the SSL error. As the purpose of this post isn’t to perform a full malware analysis but to show the tools in REMnux y MobiSec we are going to continue with the analysis of other malware which performs HTTP requests. For this second case we will use Chuli.A
The steps are the same as previously: to install the malware and run it.

In this case the malware accesses directly and IP, instead of resolving a hostname first. Luckily, REMnux is able to reply to such requests automatically hence looking at Wireshark it is possible to see that the HTTP resource requested is ‘android.php’ which it doesn’t exists in the server.

In the meantime we can see in the HTTP logs all the requests to android.php. On account that the file doesn’t exist, we are going to create it in order to interact with the malware and see what happens when targeting the resource.

Now, once the resource exists, it is possible to see the replies from the server with code 200 OK.

Probable in this POST request the malware has informed the C&C that a new device has been compromised and it sends some information about it. Likely the string ‘phone1365842571243’ sent in the POST is a unique ID.
Given the fact that the reply is 200 now the malware is able to perform other request as it is possible to see in the logs of the HTTP server. To be precise, the requested resource is ‘POST /data/phone1365842571243/process.php’. The same way than before, and in order to interact with the malware, we are going to creare such resource.

It seems it is working as there are several POST request which can be analyzed with Wireshark. This requests contains several information.
For example, in one of them the information sent looks like GPS coordinates encoded somehow.
In other one it looks like the contacts are being sent (but in this case the contact list is empty so the information sent is short)
We could continue analyzing all the request and check which information is being sent through the different POST requests but this is not the objective of this post.
The important part is to keep in mind that it is possible to use MobiSec and REMnux to interact dynamically with malware creating fake DNS replies, HTTP services, web objects, etc, while advancing in the malware analysis. Also, MobiSec integrates several tools to perform malware reverse but this will be explain in other post.