
Below a quick step-by-step guide on how to install and run the latest version of John the Ripper across several system using OpenMPI framework taking advantage of NFS to share common files. All this using Kali Linux. By creating this small environment we foster the knowledge and promote learning about different tools and techniques. The goal is understand attack methods in order to create better defenses.
Lets first review our arsenal. On all the machines we will be running Kali Linux. Kali is one of the best suites available to practice, learn and perform offensive techniques. This distribution brings the instruments needed in order to execute the steps an intruder will eventually perform during an attack. Depending on the reader’s choice, Kali Linux is available in ISO or VM. In our case we will be downloading the ISO and installing it on the different systems. Please note all the steps will be done using the privileged root account due to the Kali Linux Root Policy. Therefore is recommended you run this type of scenarios in a controlled and isolated lab environment.
We will use John the Ripper (JtR) which is a remarkable piece of software. Extremely feature rich, very fast, free and actively maintained. Today is still one of the best tools available for password cracking – definitely the best when using CPUs’ . The tool was developed by Alexander Peslyak, better known as Solar Designer. JtR can be downloaded from http://www.openwall.com/john/ and comes in two flavors. One is the official version and the other is the community-enhanced version known as “jumbo”. In this exercise we will be using the latest community edition which was released last December.
Then we will need OpenMPI. For those who might know the open source version of the MPI framework allow us to parallelize the load of JtR across multiple systems. MPI stands for the Message Passing Interface and is a API used for high-end computing topics such as parallel computing and multi-core performance. The OpenMPI implementation is developed and maintained by a consortium of academic, research, and industry partners. JtR community edition supports OpenMPI.
Finally, to share the files across the different systems we will configure the NFS protocol. In this way we will put the shared files (wordlists, dictionaries, hashes, pot file, etc..) on the master node making them accessible to any computer on the network.
The steps needed to build this setup are:
- Install and configure the network environment.
- Generate and distribute SSH keys and start SSH deamon.
- Install and configure NFS on the server and clients.
- Install OpenMPI on the master node.
- Install JtR 1.8 Jumbo edition with OpenMPI support.
- Copy hashes and wordlists to NFS share.
- Launch JtR with Mpiexec.
- Verify status and progress with skill/pkill.
For sake of brevity we will skip the first step which consists on getting the machines up and running with Kali Linux and and IP address so they can communicate between them In our case the environment looks like the following picture. A master node where we will run the NFS server and from where we will launch JtR using OpenMPI framework to distribute the load. And a set of other nodes which will have Kali Linux.

After building the mentioned environment and making sure all machines can communicate properly we go to next step. Generate and distribute SSH keys and start the SSH daemon. Essentially, generate a RSA private and public key on the master node. Then copy the public key all notes, add it to the authorized keys and change its permissions. Next, configure SSH to start during boot and start the service. These steps are illustrated below in detail.

Afterward install and configure NFS on the server and clients. To perform the installation depending on the way Kali Linux was installed and the version, the repositories might need to be updated and the GPG keys as well. To perform this the source.list file should contain the repository sources listed below and in case “apt-get update” complains about expired GPG keys the new key ring needs to be installed. Then install NFS server and Portmap (Portmap or RPCbind are the same thing). Following create a folder that will be your NFS share and change the permissions. Then this directory needs to be added to the /etc/exports file so that when NFS server starts he knows what to mount and what is the access level.. Load the config file and start the services. Finally login into each one of the nodes, create the same directory and mount it as a NFS share. These steps are illustrated below in detail.

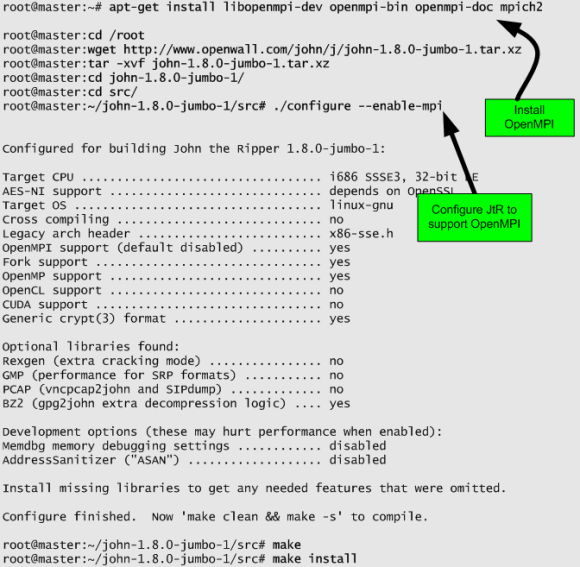
Next, on the master node install OpenMPI framework, download the latest version of JtR, uncompress, configure it with the –enable-mpi suffix and compile it. Then you need to repeat the JtR instalation steps on each one of the nodes and make sure it is installed on the same directory across all systems. These steps are illustrated below in detail. Please note the OpenMPI feature is only good when you want to run on multiple systems. if you want to run on multiple cores but just on one system you can use the -fork option when invoking JtR.
Finally, you copy the hashes and your preferred wordlist to the NFS. Then you start JtR from the master node by invoking Mpiexec. To perform that you first need a file that in this case we will call mpi-nodes.txt that contains a list of the nodes on your network and the number of CPU cores available per node. Then you run mpiexec using the -hostfile suffix and you invoke john. In this case we are running john using the default mode. It uses also a shared pot file. Note that for the shared pot file “You may send a USR2 signal to the parent MPI process for manually requesting a “pot file sync”. All nodes will re-read the pot file and stop attacking any hashes (and salts!) that some other node (or independant job) had already cracked.”

From this moment onwards you can start practice the different techniques that John allows to perform with its powerful mangling rules. The rules are available on john.conf and this version already includes the Korelogic rules. To know what the rule will do to the provided wordlist you can use the command like this “./john –wordlist=/var/mpishare/rockyou.txt –rules:Korelogic –stdout”. Below a couple of example of rules that one might want to try.

If you want to continue the journey, a proposed next step would be to further expand your skills using JtR by reading the available documentation under the doc folder where JtR was installed. Read the articles from the JtR wiki and then try out some advanced stuff like playing with KoreLogic rules and the hashes available from KoreLogic that have been used during the Crack Me if you Can contest on Defcon.
That’s it! Even though there are plenty of books and open source information that describe the methods and techniques demonstrated, the environment was built from scratch. The tools and tactics used are not new. However, they are relevant and used in today’s attacks. Likewise, the reader can learn, practice and look behind the scenes to better know them and the impact they have
From a defensive perspective choose a password that is strong enough to the point that the amount of effort an attack must spent to break it is bigger than the lifetime of the passwords. In other words, use strong passwords, don’t reuse them and change them often.
References:
http://openwall.info/wiki/john/tutorials
Click to access Rick_Redman_-_Cracking_3.1_Million_Passwords.pdf
https://www.owasp.org/images/a/af/2011-Supercharged-Slides-Redman-OWASP-Feb.pdf
http://blog.thireus.com/cracking-story-how-i-cracked-over-122-million-sha1-and-md5-hashed-passwords\
http://blog.thireus.com/category/hack1ng/crack1ng
http://pentestmonkey.net/cheat-sheet/john-the-ripper-hash-formats
 Positive Hack Days (PHD) is a well-known conference that is organized since 2011 by the company Positive Technologies. The PHD conference is held annually at Moscow and every year contains great talks and even greater CTF – Capture the Flag – challenges. One of the CTF challenges is called Hash Runner. This year Hash Runner was held during the last weekend. Hash Runner is a hands-on exercise where the participants are given the chance to test their skills at cracking passwords. Basically, there is a list of hashes available at the beginning of the contest. These hashes have been generated using a variety of algorithms and different password complexity schemes. It’s the participants job to guess the password by only having the password representation that was produced using one of the algorithms. As soon as there is a match it should be submitted to the contest. Points will be given according to the difficulty/cost of computing such the algorithm that produced the hash. For example computing LANMAN, MD5 or SHA1 hashes will give you the less points. On the other hand, algorithms such as HMAC-PBKDF2-SHA512, Bcrypt or GOST-512 will give you the most points but they are very resource intensive to compute.
Positive Hack Days (PHD) is a well-known conference that is organized since 2011 by the company Positive Technologies. The PHD conference is held annually at Moscow and every year contains great talks and even greater CTF – Capture the Flag – challenges. One of the CTF challenges is called Hash Runner. This year Hash Runner was held during the last weekend. Hash Runner is a hands-on exercise where the participants are given the chance to test their skills at cracking passwords. Basically, there is a list of hashes available at the beginning of the contest. These hashes have been generated using a variety of algorithms and different password complexity schemes. It’s the participants job to guess the password by only having the password representation that was produced using one of the algorithms. As soon as there is a match it should be submitted to the contest. Points will be given according to the difficulty/cost of computing such the algorithm that produced the hash. For example computing LANMAN, MD5 or SHA1 hashes will give you the less points. On the other hand, algorithms such as HMAC-PBKDF2-SHA512, Bcrypt or GOST-512 will give you the most points but they are very resource intensive to compute.






